APRIL 2025 HACK ANALYSIS
Author: Sisi
April 2025’s $357 million loss across the ecosystem represents a sobering inflection point for our industry. This isn’t just another month of exploits, it’s a comprehensive blueprint of how hackers are evolving their tactics and tool against the increasingly complex web3 infrastructures.
What makes April’s attacks particularly concerning for is the sophistication, diversity and scale.
Here are major incident and the security lessons
1. The $330.7M Bitcoin Transfer: Evolution of Phishing
DATE: April 3, 2025
VECTOR: Phishing & Social Engineering
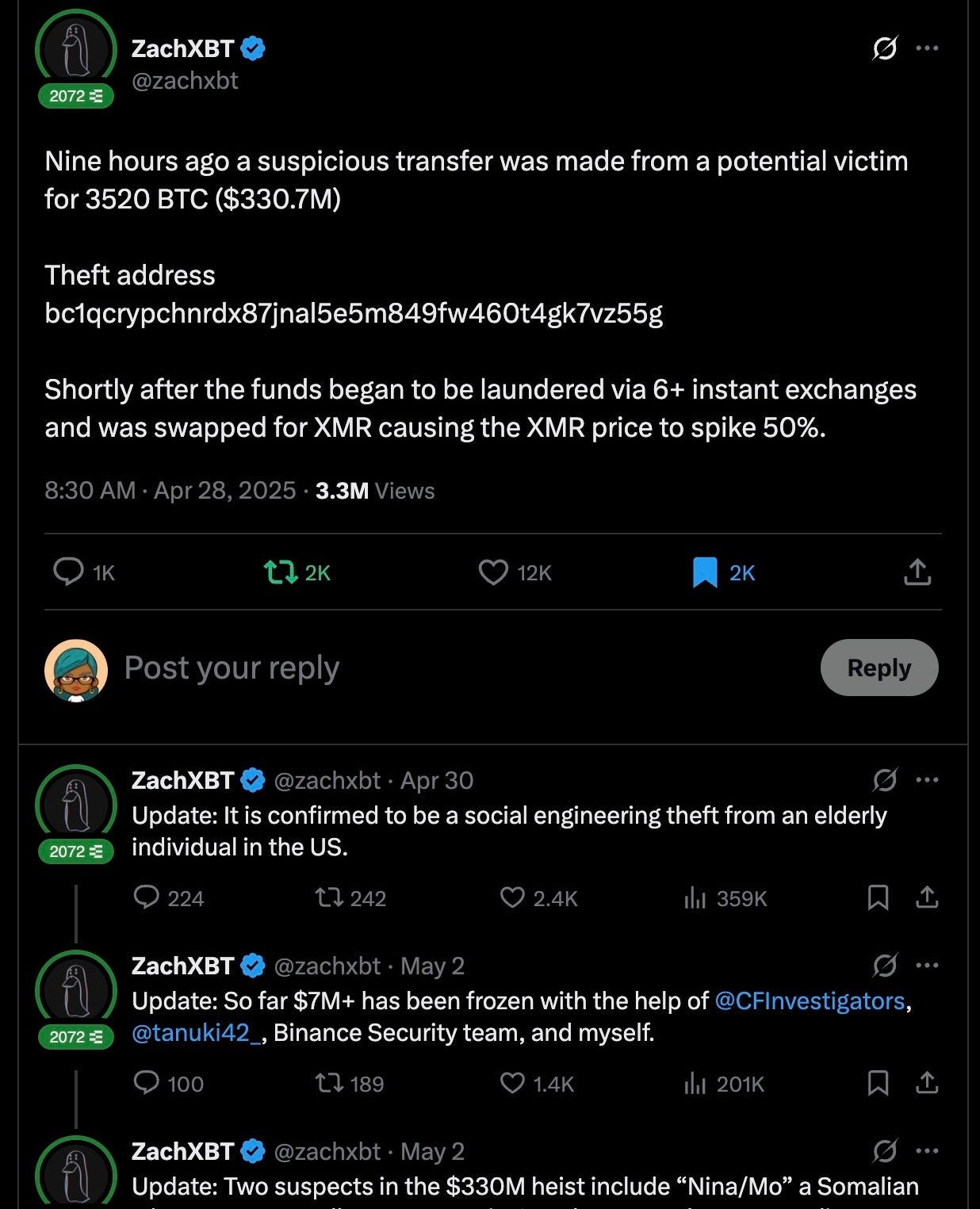
April’s largest hack that accounts for 92% of all losses happened on April 28, a staggering 3,520 BTC valued at approximately $330.7 million was illicitly transferred from the wallet of an elderly U.S. citizen. The hacker used a sophisticated social engineering techniques to gain unauthorized access to the victim’s private keys. Using over 300+ wallets and 20 exchanges, the BTC was laundered. Converted into Monero (XMR) which result in nearly 40 % spike following the hack. The funds are nearly untraceable due to privacy centric cryptocurrency.
From ZachXBT Twitter
This hack demonstrates how phishing has evolved from dm scams to sophisticated psychological operations.
This hack likely incorporated
Technical sophistication: Advanced malware designed to intercept wallet credentials or hijack transaction signing processes
Social engineering complexity: Targeted approaches that leveraged specific knowledge of victim’s holdings and behavioural pattern
Timing precision: Attacks coordinated around market movements when large transfers wouldn’t appear abnormal
The scale of this attack suggests whale level targets. Traditional security advice like “check the URL” is clearly insufficient against attacks that can trick even experienced users into believing they’re performing legitimate transactions.
Recovery Status: No funds recovered as of this report date but 7m+ has been frozen so far.
2. KiloEx’s $8.4M EXPOILT: A Verification Gap
DATE : April 11, 2025
VECTOR: Oracle Manipulation via MinimalForwarder Flaw
KiloEx, a decentralized perpetual contract trading platform suffered a $7.5 million loss due to a vulnerability in its price oracle system. Hacker manipulated the oracle to execute trades at favorable rates draining funds from the platform.
The KiloEx exploit represents a classic smart contract vulnerability, a failure to verify transaction origins in the MinimalForwarder contract.
The instructive here are :
The vulnerability existed in a forwarding mechanism, which often receives less security scrutiny than core functionality
It highlights how auxiliary contracts can create systemic risk
The team’s rapid response enabled a complete mitigation strategy
Recovery Status: 100% of funds recovered within 48 hours through swift response by the KiloEx team, who implemented an emergency protocol and were able to freeze and recover the stolen assets.
This incident demonstrates how security blind spots often exist in the “connective tissue” between contract systems rather than in the primary business logic that receives the most audit attention.
3. UPCX’s $70M Private Key Compromise
VECTOR: Centralization Problem
DATE: April 17, 2025
The UPCX attack represents one of Web3’s most persistent vulnerabilities, “centralized points “ of failure in supposedly decentralized systems.
This attack leveraged:
Access to privileged management wallets
The ability to execute contract upgrades
Likely internal system compromise or insider threat vectors
Recovery Status: No funds recovered as the hacker quickly moved assets through multiple chains and mixing services.
The hard truth is that many protocols maintain governance mechanisms with significant centralized control, creating high value targets for hackers. This is as much an architectural problem as it is a key management issue.
4. Loopscale’s $5.8M Logic Flaw: The Composability Challenge
DATE: April 22, 2025
VECTOR: Composability Misunderstanding in Token Pricing
Loopscale is a solana based DeFi protocol exploited for $5.8 million due to a flaw in the pricing mechanism of its RateX PT tokens. The hacker manipulated token prices to obtain under collateralized loans, effectively draining the protocol’s funds. In a turn of events, the hacker returned the stolen assets in exchange for a 10% bounty
The Loopscale attack highlights how contract interaction vulnerabilities can emerge from seemingly secure individual components. The $5.8M loss stemmed from
Flawed assumptions about how different contracts would interact
Possible price manipulation vectors
Unchecked external calls creating unexpected execution paths
Recovery Status: Partial recovery, approximately $1.2M (20%) was frozen before the hacker could move it off chain.
This exemplifies why isolated security reviews often miss vulnerabilities that only emerge when contracts operate within the broader DeFi ecosystem. Security needs to consider composability, not just isolated contract logic.
5. MorphoLabs’ $2.6M Front-End Hijack
DATE: April 29, 2025
VECTOR: Web2 Frontend Exploit
While blockchain enthusiasts focus on on chain security, MorphoLabs’ frontend compromise demonstrates how Web2 vulnerabilities can also be critical attack vectors:
Interface manipulation redirected users to malicious contracts
Backend infrastructure remained intact while users lost funds
UI/UX elements that users trust for verification were compromised
Recovery Status: No funds recovered as transactions were technically valid from an on chain perspective.
This attack required no on-chain exploits whatsoever, it’s a powerful reminder that web3’s security is only as strong as its weakest access point.
Pattern Analysis: The Security Gaps Exploited
Looking across these incidents, several patterns emerge that demand more attention
1. The Phishing Renaissance (94% of Losses)
Phishing has evolved from a nuisance to the dominant threat vector. Modern phishing operations now involves
Deep research into target behaviors and holdings
Creation of comprehensive fake environments, cloned dApps, wallet interfaces
Sophisticated social engineering that leverages time pressure and FOMO
The scale of April’s losses suggests attackers have industrialized these approaches, creating phishing infrastructure that can target hundreds to thousands of users simultaneously.
2. The Centralization Paradox
Despite decentralization being a core value of, many protocols maintain highly centralized security architectures:
Single admin keys controlling upgradeable contracts
Privileged access without time locks or multi-signature requirements
Hot wallets holding excessive assets or permissions
UPCX’s $70M loss demonstrates how these centralized components create catastrophic single points of failure.
3. The Composability Challenge
Smart contracts don’t operate in isolation, yet they’re often secured as if they do:
Inter contract calls create complex execution paths
Price oracles introduce external dependencies
Shared liquidity pools create systemic risks
Loopscale’s exploit shows how vulnerabilities emerge from these interactions rather than from individual contracts.
4. The Interface Blind Spot
The MorphoLabs attack highlights our industry’s tendency to focus on blockchain security while neglecting Web2 infrastructure:
DNS security remains inconsistent
Front-end hosting often lacks proper security controls
Interface verification mechanisms are insufficient
Recommended Security Architecture Overhaul
April’s attacks demand more than incremental improvements, it also require a fundamental rethink of web3 security:
For Protocol Developers
Move beyond audit-centric security: Implement continuous monitoring, formal verification, and adversarial testing
Assume compromise: Design systems where no single breach can lead to catastrophic losses
Minimize centralization: Replace admin keys with decentralized governance mechanisms
Implement defense in depth: Create multiple security layers that must all be bypassed for successful attacks
For Infrastructure Providers
Secure the entire stack: Treat frontend security with the same rigor as on chain security
Implement hardware security modules (HSMs) for all critical key management
Develop attestation mechanisms for front-end integrity verification
Create anomaly detection systems for rapid response to unusual transaction patterns
For Users
Apply zero trust principles to every transaction
Verify every interaction regardless of source
Practice strict asset compartmentalization: Use separate wallets for different purposes and risk levels
Implement simulation-before-execution: Preview transactions before signing
Maintain security hygiene: Regular permission reviews and revocations
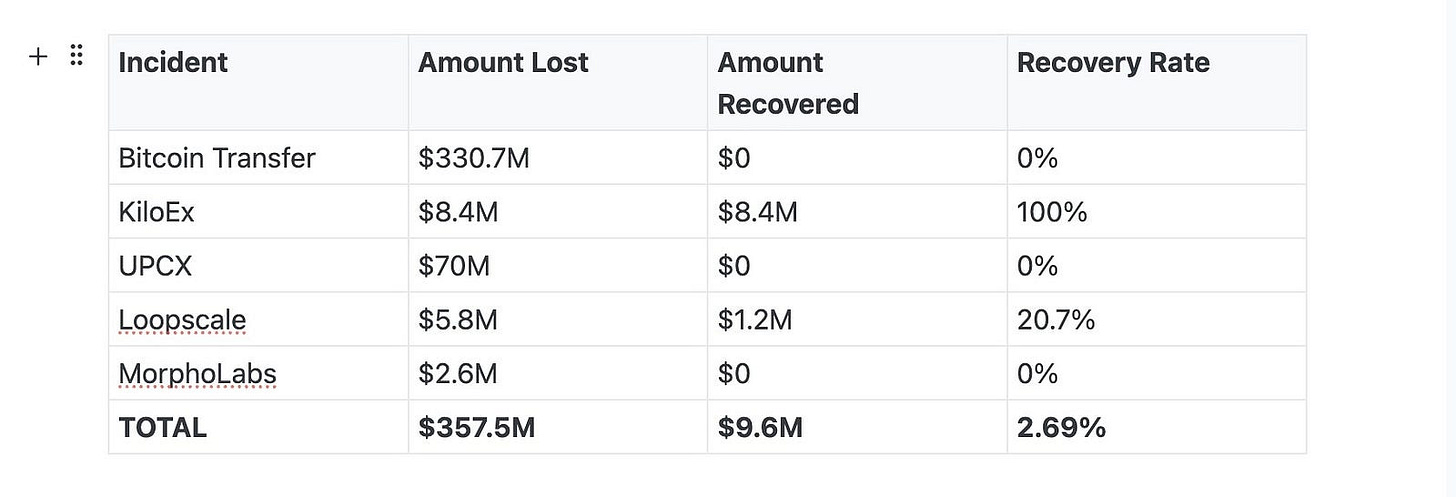
April 2025’s $357 million in gross losses (approximately $347.4 million in net losses after recoveries) should serve as a watershed moment for the web3. The attacks demonstrate that our current security approaches are fundamentally inadequate against evolved threat actors.
This dismal recovery rate of less than 3% underscores the reality that in Web3, prevention remains vastly more effective than recovery. The KiloEx incident stands as a notable exception rather than the rule of thumb, highlighting how properly designed circuit breakers and response plans can make a difference.
The industry faces a choice: continue treating security as a compliance exercise with predictable periodic losses, or embrace a security first mindset where protection of user assets becomes the primary design consideration.
The technical solutions exist. The question is whether we collectively have the will to implement them before the next potentially larger wave of attacks forces our hand?