SlowMist: 2024 Q2 MistTrack Stolen Funds Analysis
Author: SlowMist
As blockchain technology rapidly advances, security incidents like theft, phishing, and fraud are becoming more frequent and diverse. SlowMist receives numerous daily requests for assistance from victims, including those who have lost millions of dollars. This article compiles and analyzes quarterly stolen fund reports, using anonymized real cases to highlight common and uncommon malicious tactics, aiming to help users better protect their assets.
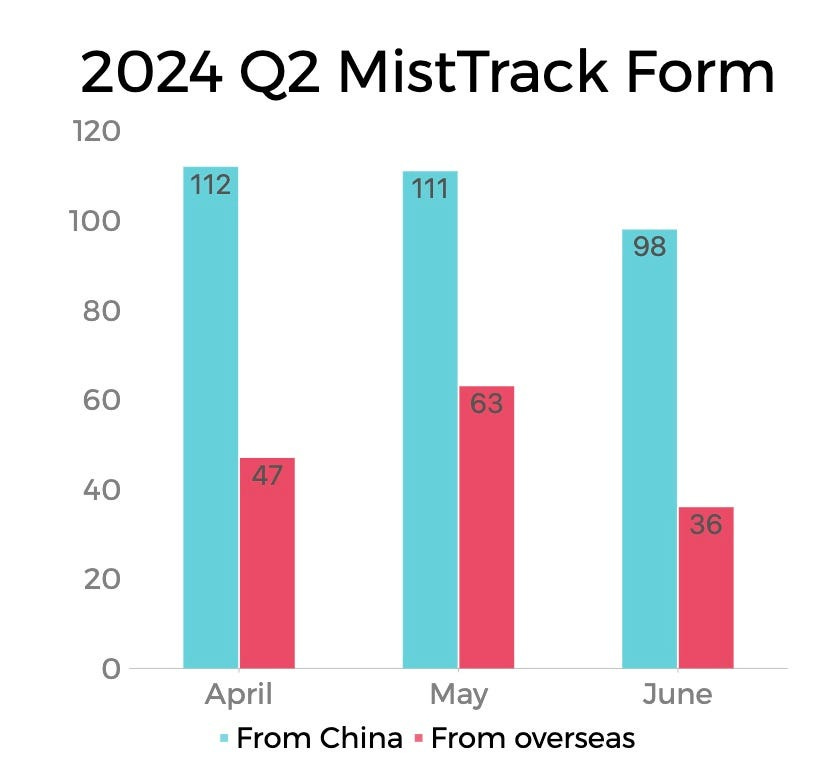
In Q2 2024, the MistTrack Team received a total of 467 stolen fund reports, including 146 from overseas and 321 from domestic sources. We provided free assessment services for these cases (Note: The content of this analysis only includes cases submitted via our form and excludes those contacted through email or other channels).
Among these, our team assisted 18 victims in freezing approximately $20.66 million in funds across 13 platforms.
Top 3 Causes of Theft in Q2 2024
The most common causes of theft in Q2 2024 are as follows
Private Key Leaks
According to the Q2 reports, many users store their private keys or mnemonic phrases in cloud storage services such as Google Docs, Tencent Docs, Baidu Cloud, and Shimo Docs. Some users send their private keys or mnemonic phrases to trusted friends via tools like WeChat, and some even use WeChat’s image-to-text feature to copy mnemonic phrases into WPS spreadsheets, encrypt them, and enable cloud services while also storing them on local hard drives. These actions, which seem to enhance information security, actually greatly increase the risk of information theft. Hackers often use “credential stuffing” techniques, trying to log into these cloud services with databases of leaked account credentials found online. If successful, they can easily find and steal crypto related information. There are also cases of phishing, such as victims being tricked by scammers posing as customer service agents into providing their mnemonic phrases or being deceived by phishing links on platforms like Discord to input their private key information. The MistTrack Team strongly advises that private keys or mnemonic phrases should never be disclosed to anyone under any circumstances.
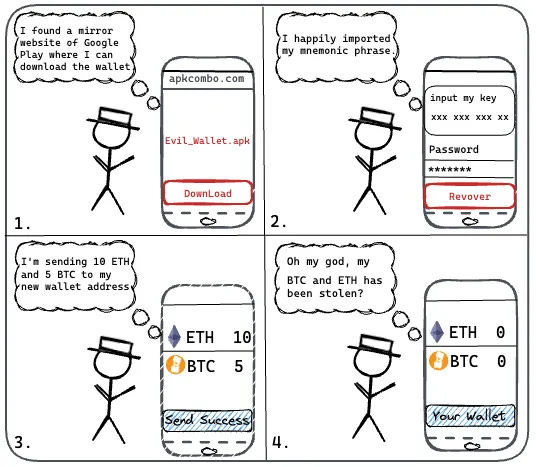
Fake wallets are another major cause of private key leaks. Despite being an old issue, many users still inadvertently click on ads while using search engines and download fake wallet apps. Many users choose to download applications from third-party sites due to network reasons. Although these sites claim that their apps are mirrored from Google Play, their actual security is questionable. The SlowMist security team previously analyzed wallet apps on the third-party market apkcombo and found that the imToken 24.9.11 version offered there is non-existent and is currently the most common fake imToken wallet version.
We have also tracked down some backend management systems related to fake wallet teams, which include complex digital currency control functions such as user management, currency management, and deposit management. The advanced nature and professional level of these phishing activities far exceed our expectations.
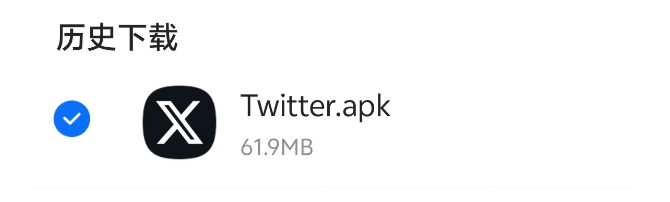
For example, in Q2, there was a rare case where a user searched for “Twitter” on a search engine and accidentally downloaded a fake Twitter app. When the user opened the app, a prompt appeared, claiming that regional restrictions required the use of a VPN. The app then directed the user to download a built-in fake VPN, which resulted in the user’s private key or mnemonic phrase being stolen. This case serves as a reminder that all online applications and services should be carefully scrutinized and verified to ensure their legitimacy and security.
Phishing
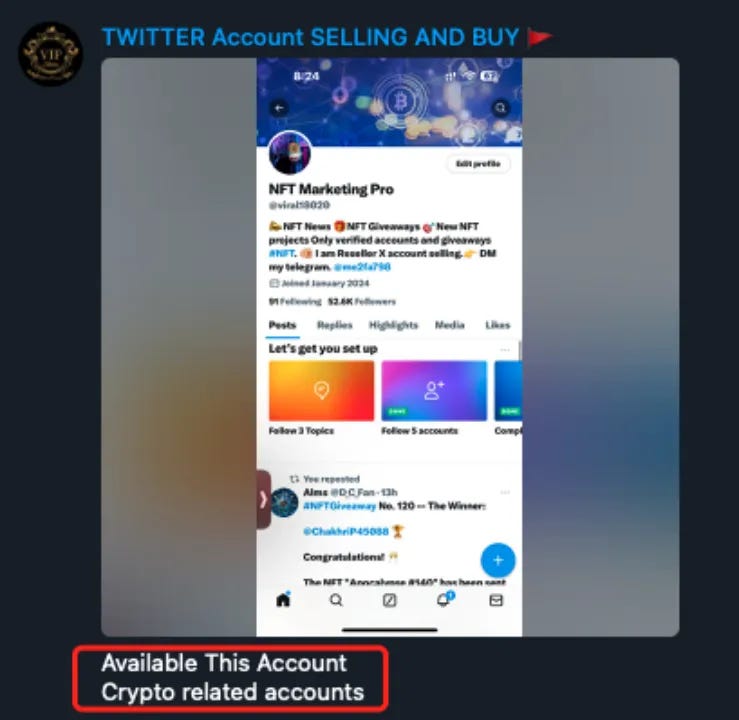
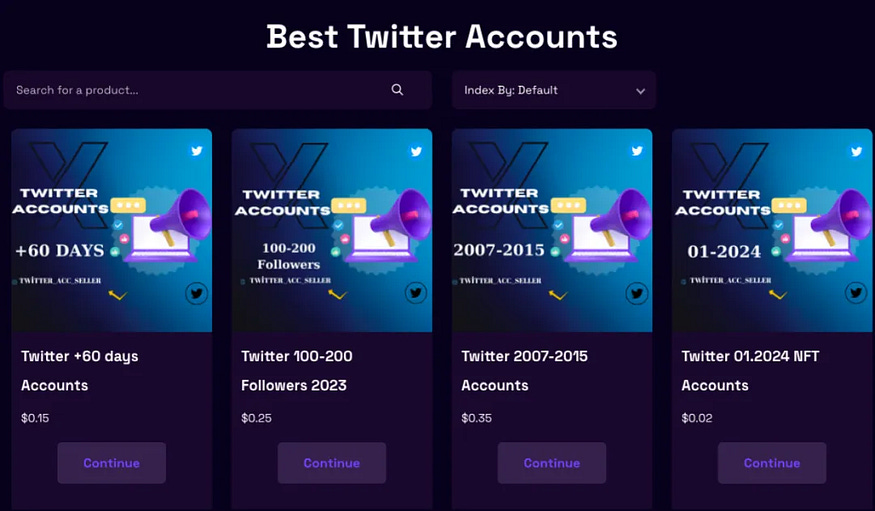
Analysis shows that in Q2, many theft incidents were caused by phishing, specifically through users clicking on phishing link comments under tweets from well-known projects. A previous targeted analysis by the SlowMist security team revealed that approximately 80% of the first comments under tweets from prominent project accounts are occupied by phishing scam accounts. Additionally, we discovered numerous Telegram groups selling Twitter accounts, with varying numbers of followers, posts, and different registration times, allowing potential buyers to choose accounts based on their needs. Historical data indicates that most of these sold accounts are related to the cryptocurrency industry or influencers.
Additionally, there are websites specifically dedicated to selling Twitter accounts, offering accounts from various years, and even providing highly similar accounts for purchase. For example, a fake account named “Optimlzm” can look almost identical to the real account “Optimism.” After purchasing the highly similar account, phishing groups use promotion tools to boost the account’s interactions and follower count, thereby increasing its credibility. These promotion accounts accept cryptocurrency payments and offer various social platform services, including likes, retweets, and followers. By leveraging these tools, phishing groups can acquire a Twitter account with a large number of followers and posts, closely mimicking the activity of the official project accounts.
The phishing groups then carry out their schemes, such as using automated bots to follow and track the activities of well-known projects. When a project posts a tweet, the bot automatically responds to secure the top comment spot, attracting more visibility. Given the high similarity between the disguised phishing account and the official project account, many users find it challenging to distinguish between the two. This increases the phishing group’s success rate. If users are not careful and click on the phishing links from these fake accounts, they’re at risk of losing their assets.
Overall, in the blockchain industry, phishing attacks primarily pose risks to users through “domains” and “signatures.” To achieve comprehensive security protection, we advocate a dual defense strategy: user awareness and technical measures.
Technical measures involve using various tools, such as the phishing risk blocking plugin Scam Sniffer, to ensure asset and information security. These tools provide timely risk alerts when users open suspicious phishing pages, blocking threats at the earliest stage.
User awareness is equally important. We strongly recommend that users thoroughly read and gradually master the Blockchain Dark Forest Survival Guide.
By combining these two defense strategies, users can effectively counter the ever-evolving phishing attack methods and safeguard their assets.
Fraud
There are many types of scams, but the most common in Q2 was the honeypot scheme. In cybersecurity, a honeypot is a system set up to attract attackers by appearing as a legitimate target, only to trap them once they engage. Similarly, in this scam, digital currencies are designed to lure investors with attractive prospects, but once purchased, they cannot be sold.
A victim shared their experience: “I asked a question in a Telegram group, and someone enthusiastically answered and taught me a lot. After chatting privately for two days, I felt they were quite trustworthy. They suggested I invest in a new token in the primary market and provided me with a contract address on PancakeSwap. After I bought it, the token’s value kept rising. They told me it was a once-in-six-months golden opportunity and urged me to invest more. Sensing something was off, I didn’t follow their advice, but they kept pushing me. When I asked others in the group to help investigate, I discovered it was indeed a honeypot token. I could buy but not sell it. Once the scammer realized I wouldn’t invest more, they blocked me.”
This victim’s experience reflects the typical pattern of a honeypot scam:
1. The scammer sets up a smart contract with traps and baits victims with promises of high profits.
2. The scammer aggressively entices the target to buy the token. After the victim purchases it, they often see the token’s value rise quickly. The victim usually decides to wait until the token’s value increases significantly before attempting to sell, only to discover they cannot sell the token.
3. Finally, the scammer extracts the victim’s invested funds.
It is worth noting that most honeypot incidents mentioned in the Q2 reports occurred on the Binance Smart Chain (BSC). These coins showed a lot of trading activity, and scammers would send tokens to various wallets and exchanges to create the illusion of widespread participation.
Due to the inherently deceptive nature of honeypot schemes, even experienced investors may find it challenging to recognize the scam. With the rise of meme coins, various types of “shitcoins” are impacting the market. The rapid price increase of honeypot coins often leads to impulsive purchases, and many unsuspecting market participants chase this “shitcoin craze,” only to fall into the trap where they cannot sell the tokens.
Therefore, the MistTrack Team recommends users take the following measures before making transactions to avoid losses from honeypot schemes:
Use MistTrack to check the risk status of the relevant address or utilize GoPlus’s Token Security Detection tool to identify honeypot tokens and make informed trading decisions.
Verify on Etherscan or BscScan whether the code has been audited and validated, or read related comments, as some victims may post warnings in the scam token’s comment section.
Research the virtual currency information and consider the project team’s background to enhance self-protection awareness. Be wary of cryptocurrencies promising exceptionally high returns, as such returns typically come with higher risks.
Final Note
If your cryptocurrency has unfortunately been stolen, we offer free community assistance services for case evaluation. You only need to submit a form following the classification guide (funds stolen/scammed/ransomed). The hacker addresses you submit will also be synchronized to SlowMist’s InMist Threat Intelligence Network for risk control.
Chinese: https://aml.slowmist.com/cn/recovery-funds.html
English : https://aml.slowmist.com/recovery-funds.html).
SlowMist has been deeply involved in the anti-money laundering field of cryptocurrency for many years, developing a comprehensive and efficient solution that covers compliance, investigation, and auditing. We actively contribute to creating a healthy cryptocurrency ecosystem and provide professional services to the Web3 industry, financial institutions, regulatory bodies, and compliance departments.
MistTrack is a compliance investigation platform offering wallet address analysis, fund monitoring, and tracking. It has accumulated over 300 million address tags, more than a thousand address entities, 500,000+ threat intelligence data points, and 90 million+ risk addresses. These resources provide robust protection for the security of digital assets and the fight against money laundering.