Understanding Lazarus: The Real Threat to the Crypto Industry
Author: Tay
Crypto folks (hopefully) already know that Lazarus is one of the most prevalent threat actors targeting this industry. They rekt more people, companies, protocols than anyone else. But it's good to know exactly how they get in. Bc another smart contract audit won't save you.
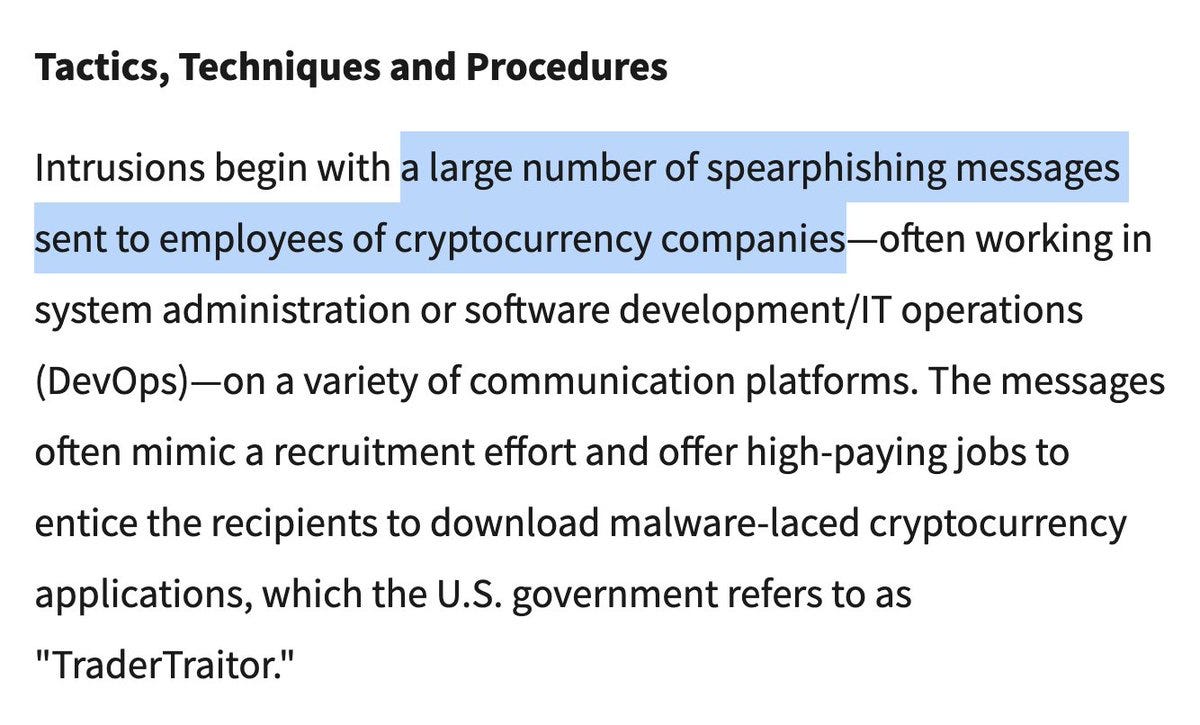
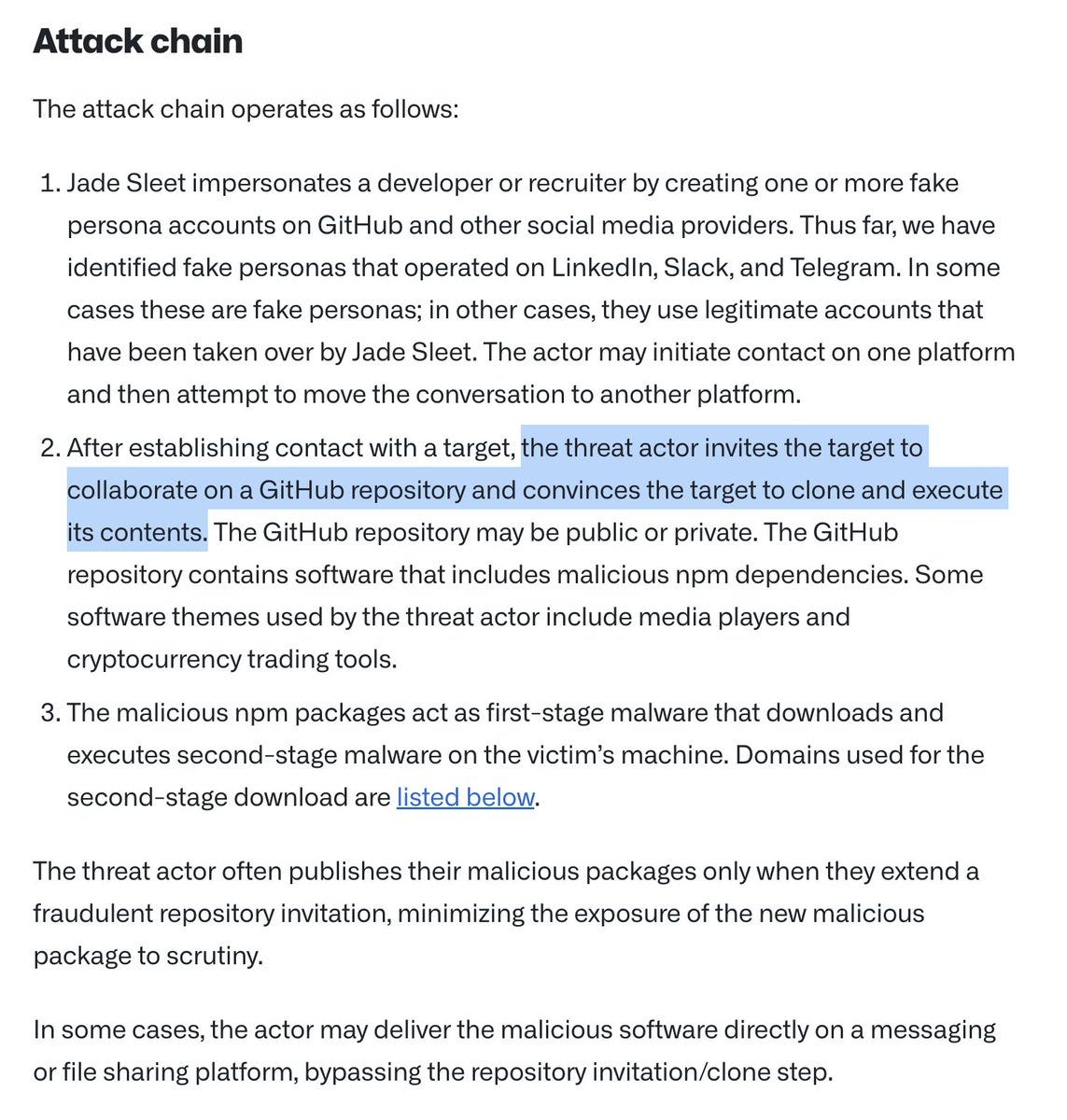
For example, one long-time fave method: - Contact employee via social/messaging app - Direct them to a Github for a job offer, "skills test," or to help with a bug - Rekt individual's device - Gain entry to company's AWS - Rekt company (and their users) cloud.google.com/blog/topics/th…
With permission, I’m sharing a recent convo that led to $2m+ stolen so you can see how this DPRK crew (TraderTraitor) is operating today. These convos are pretty rare to see. Thefts occur months later, so very few uncover how the initial entry was made. cisa.gov/news-events/cy…
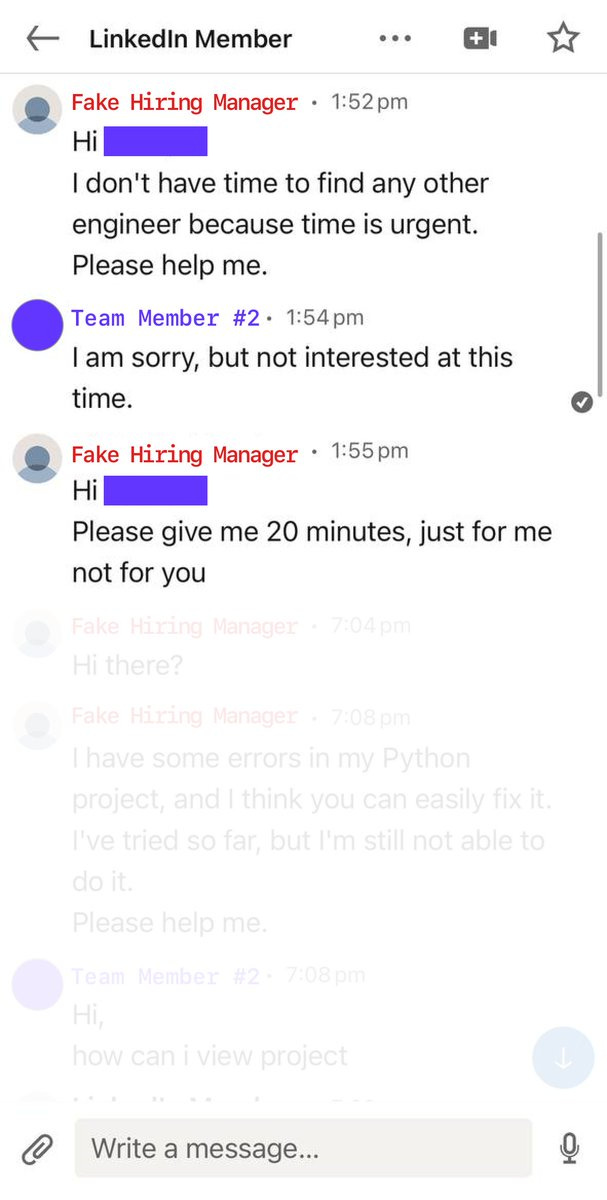
This particular example is also notable because we have records of two separate convos. Same threat actor, using the same Linkedin persona, reaching out to technical employees at the same company...at the same time.
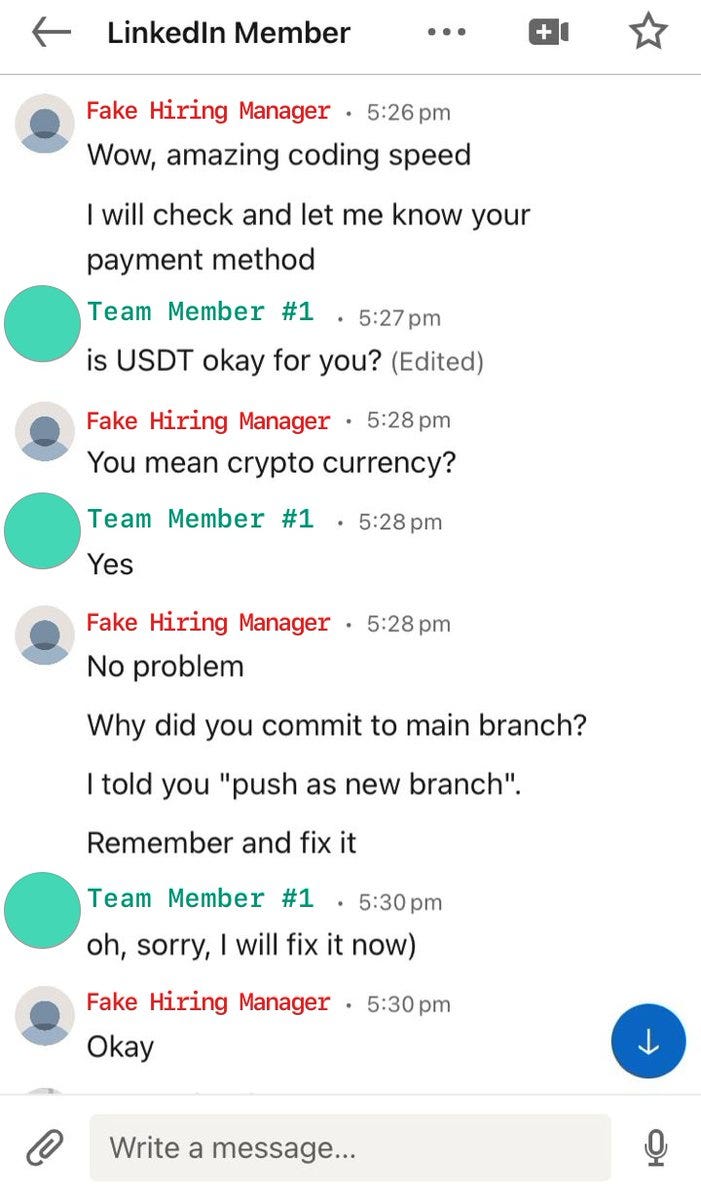
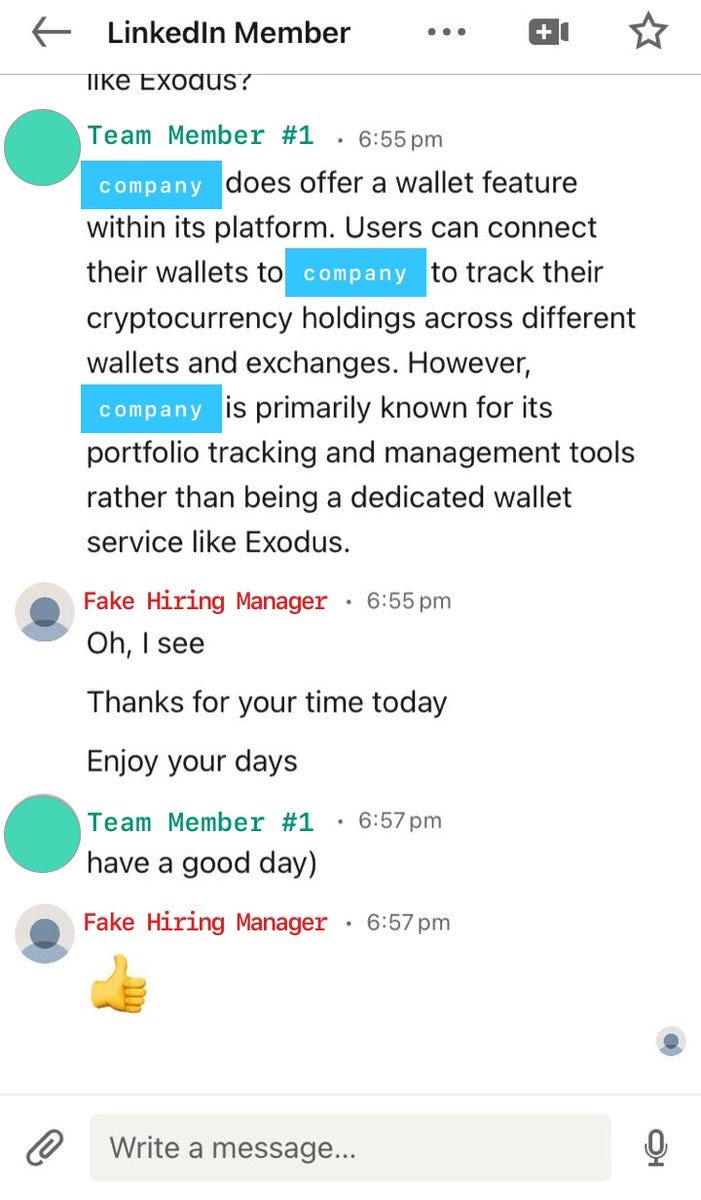
And, even though Team Member #2 declined, the attacker continued right along with the first team member. They quickly added that individual to a private Github repo, asked him to make sure he could successfully run the build, and then asked for help resolving an error.
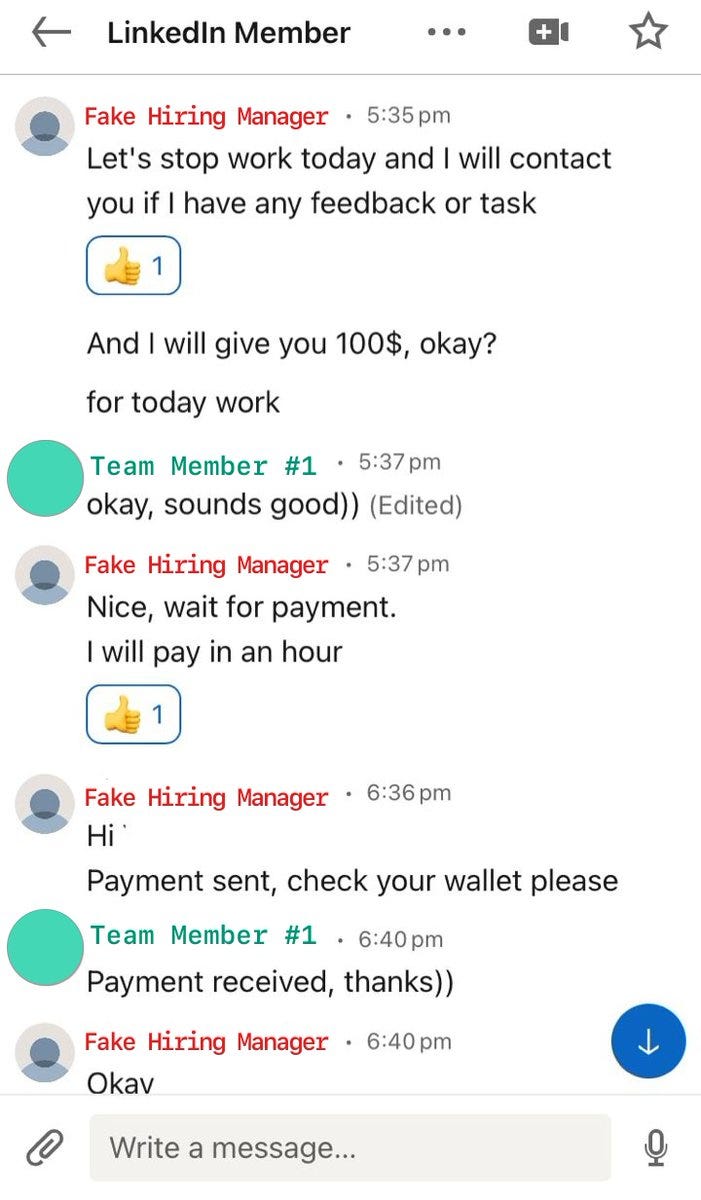
This team member's device was compromised as soon as he built the code (~4:46pm) However, the attacker never let on and continued to talk and ask questions. Through it all, the employee’s wallets were not drained. In fact, the attacker offered to pay him for his help.
Not only that, but she actually tells him she will pay “in an hour” and then, exactly 59 minutes later, she actually sends him $100 USDT on Tron for his help. Just as he requested.
From there, the fake persona “keeps connecting” (
) with the target. As it turns out, this team member had actually left the company shortly before. He no longer had access to any systems—a fact the attacker may have determined on their own between ~4:46pm and ~6:40pm.
And with that, the conversation wraps up with Team Member #1. They'll never speak again. Only moments later though, the attacker will return to Team Member #2 and start all over again.
The conversation is the same the second time around except that: 1. The repo is now public (no waiting around to accept the invite?) 2. The conversation is cut short when he asks about the legitimate profile of the person that this attacker was impersonating (awkward!)
The employee clearly felt something about this person/interaction was sus. But he never realized that they had already landed the malware. Which makes sense—it's a seemingly benign interaction, nothing crazy happened, and no theft would occur for over a month.
I know some of you are thinking, “I would never fall for this!” That's stupid, stfu. They go after everyone: executives, frontend devs, backend devs, even biz dev. They use everything: TG, X, Discord, Email, Slack, etc. Your takeaway should NOT be to avoid Linkedin.
Your takeaway should be that really sophisticated threat actors are targeting you, your team, your products all the time. They do this shit all day, every day. They constantly evolve. Their methods work. github.blog/2023-07-18-sec…
Instead of thinking you're invincible: Eliminate single points of failure Use hardware wallets / hardware MFA Don't run/build code from strangers Use diff devices for talking vs accessing crypto Don't judge Learn from other's mistakes Educate those around you STAY SKEPTICAL!