Author: Beosin
1 Crypto theft cases
1.1. A wallet of Bo Shen, founding partner of Fenbushi Capital, was stolen
On November 23, 2022, according to Beosin EagleEye, a security monitoring, real-time warning and interdiction platform of Beosin, Bo Shen, founding partner of Fenbushi Capital, said on twitter: "My wallet ending in 894 with a total value of $42m including 38M USDC was stolen in the early hours of November 10 New York time. Stolen assets are my personal funds, not funds of Fenbushi. The case has been reported to local police and the FBI and my lawyers are involved."
Case Analysis
The Beosin security team analyzed the transactions of USDC and located a number of thefts at Bo shen's address ending in 894, one of which is shown below :
0xf6ff8f672e41b8cfafb20881f792022f6573bd9fbf4f00acaeea97bbc2f6e4f7。
Since the transaction was revoked by the address0x6be85603322df6DC66163eF5f82A9c6ffBC5e894, this crypto theft was caused by private key leak.
Most of the stolen funds have been converted into DAI and transferred by the attackers to the following two addresses:0x4ac9ca41efe0ea19b8f3493a91d8a5f706e1e8f9,0x66F62574ab04989737228D18C3624f7FC1edAe14.
There were 1606 ETH left in 0x24B93EED37e6FfE948A9bdF365d750B52AdCBC2e.
we want to remind users to attach great importance to wallet security again. Beosin Trace is continuously monitoring the hacker's addresses. The total loss of Bo Shen is shown below :
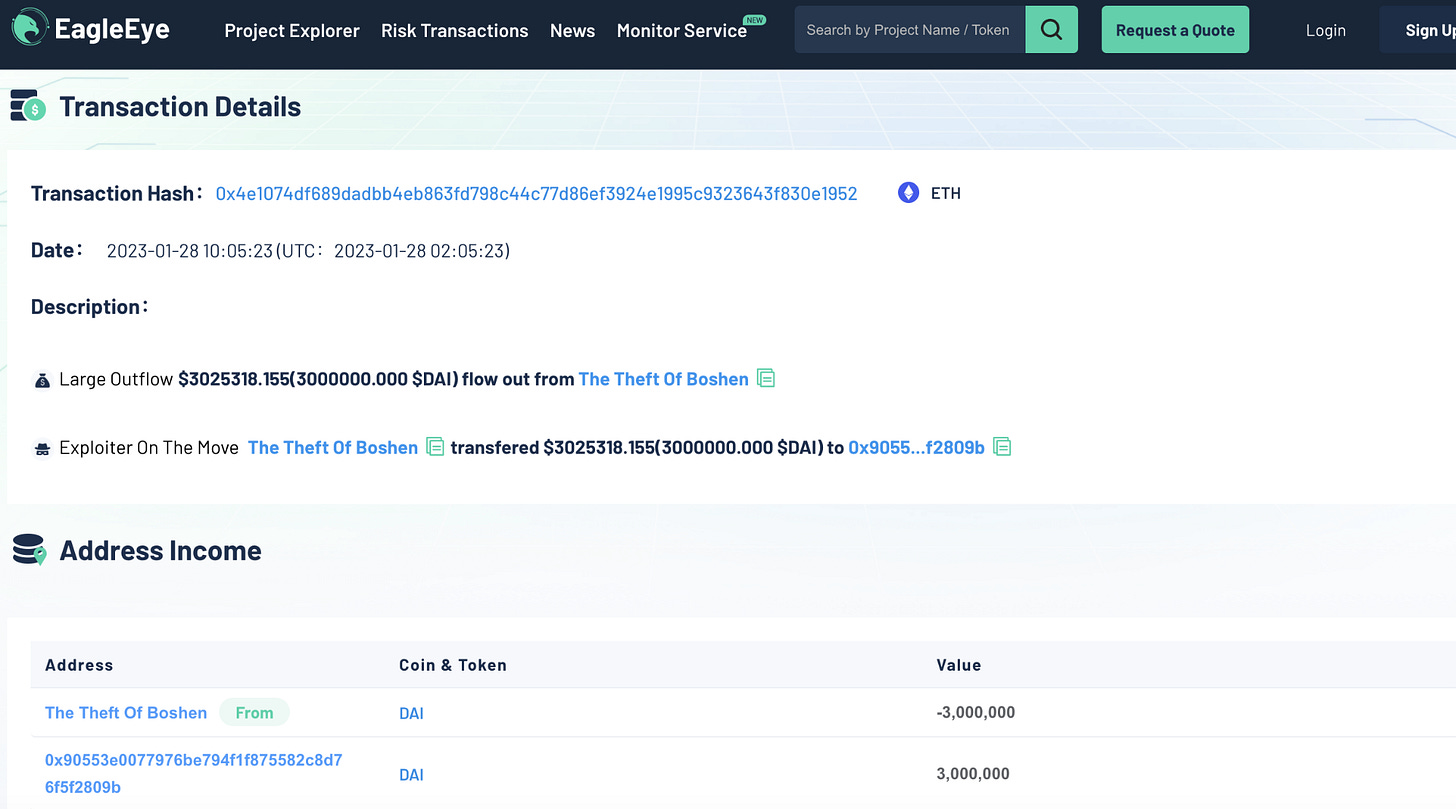
On January 28, 2023, Beosin EagleEye found that the stolen funds of Bo Shen, founding partner of Fenbushi Capital, were moved by the attackers. One of the attackers' address 0x66F62574 transferred 4M DAI to 0x90553e00, which were then swapped into 2496.66 ETH. These ETH tokens were then transferred to 0x376A0255 and 502 of these tokens were sent to FixedFloat. There were 1994.65 ETH left in 0x376A0255 and Beosin Trace would keep monitoring these addresses.
1.2. A popular crypto influencer was hacked and lost all of his digital assets
On January 15, 2023, another security incident was detected by Beosin EagleEye security monitoring, real-time warning and blocking platform. The victim of this security incident is a crypto KOL: NFT God. He tweeted that hackers stole all of his crypto assets and NFT by hacking into his Twitter, Substack, Gmail, Discord and wallets, and also posted phishing links through the stolen accounts. The loss was triggered by the fact that his Ledger had previously been set up as a hot wallet instead of a cold wallet on his new device. The mnemonics were imported for wallet use on internet-connected computers. Yesterday after downloading OBS for a live game broadcast, he clicked on Google's sponsor link and downloaded a malware, giving hackers access to his crypto assets.
This shows that security incidents often happen on big crypto influencers and there are more crypto thefts of ordinary users. Due to the characteristics of crypto assets, it is a more serious challenge to protect users' digital assets compared to Web2. With the maturity of blockchain technology, the value of blockchain applications becomes more and more notable. The economic benefits carried by blockchain ecosystem increase every year, and the security risk becomes more and more serious and the crime of hackers has become more rampant.
2 What are the types of crimes related to crypto?
Crypto crimes are that criminals aim at obtaining the crypto assets of others directly, or by theft, fraud, robbery and other acts. The most common crime is crypto theft:
Steal crypto asstes by hacking or other computer techniques
Defraud/steal people's accounts and private keys to steal crypto assets
Use phishing links/platforms to entice people to click on the links or enter the platforms to enter personal identity, accounts and other privacy information to steal crypto assets
Obtain people's crypto assets through robbery
Additionally, there are some frauds aiming to stealing people's cryptocurrencies:
Use fake crypto exchange platforms to cheat victims to deposit crypto assets such as Bitcoin, Ether, and USDT, into the platform. The profit and loss data that victims see are made by criminals at the background. Victims can not withdraw money and eventually criminals carry victims' crypto assets and run away.
Use fake crypto investments to trick victims into buying a project token by crypto assets such as Bitcoin, Ether, or USDT. Then criminals will claim that the project token will be listed on major exchanges soon and the token price will grow tens or even hundreds of times. In fact, the project token is worthless, and will not be on the exchange at all. The real goal of criminals is to obtain investors' cryptocurrencies.
Scam crypto assets by offering investment services such as fake agents to help make crypto investments. Once your cryptocurrencies are transferred to them, the criminals would disappear with the victims' crypto assets.
3 The characteristics of crypto assets bring obstacles to criminal investigation
In addition to the characteristics of non-physical state, value storage, digital storage and payment usage, crypto also has some typical characteristics, which can not only provide greater convenience for illegal crimes but also brings more difficulties and obstacles to criminal investigation, making it easier to become a fertile soil for a series of new crimes and a preferred tool for underground industries. The main features of crypto that deserve emphasis are as follows:
Decentralized
The issuance and trading of crypto does not rely on the support of governments, central banks and enterprises, or the services provided by credits and traditional financial institutions, but through the network protocol which can achieve a direct interaction between one node and the other nodes. Since all nodes are the center, there is no center, which makes it more convenient for criminals to use crypto as a tool to commit crimes.
Anonymous
Most crypto assets are in the form of P2P special technology, which realizes the protection of privacy through the exchange of value between addresses, that is, creating different addresses for each transaction. Thus, transactions have a strong anonymity and bring a lot of obstacles to the supervision and criminal investigation.
Exchangeable globally
Although some countries prohibit the exchange of crypto with fiat currency, crypto can be freely circulated in the world by peer-to-peer network nodes based on the global network. People can still achieve to exchange for crypto by various means.
Easy to trade
Users only need to use network and electronic accounts to complete crypto transactions in peer-to-peer networks. These transactions are anonymous and do not need to go through the regulatory authorities. Compared with the traditional currency, crypto has a strong advantage of convenience but it is easy to become an important tool of money-laundering.
4 How to handle or report if your crypto assets are stolen?
Since law and policy is different from country to country, you should report your case and seek for help based on the local law when your crypto assets are stolen. The following steps are steps that every victim should take to minimize his/her loss:
Step 1: transfer any remaining assets
If an attack on a wallet results in the theft of assets, the remaining assets in the wallet should be immediately transferred to other wallets, and discard the wallet under attack.
If it is not possible to discard or transfer remaining assets immediately, check the account authorizations and cancel all authorizations on time.
If the stolen assets are NFT, if there is a way to freeze them, contact the project party immediately for an asset freeze.
Step 2: seek help from a security team and track funds
This step, whether the victim is a project or an individual, is to seek the assistance of a professional security team as quickly as possible to keep track of the stolen funds. Professional security teams will generally have a wealth of experience in security analysis and tracing funds. They can find where the problem lies from a professional point of view.
More importantly, in the case of stolen money, it is necessary to trace the stolen assets, whether the attacker has sold it for stable coins, and find the moving direction of the stolen funds, such as leaving them in the attacker's wallet, or transferring them into exchanges, or into a coin mixer, and so on. These on-chain trackings can know where the funds go.
Another kind of tracing is offchain tracing, through the traditional network security means to obtain the attacker's IP information, server information, mailbox information, mobile phone number, etc. Through the joint law enforcement agencies to find the personal information of the attackers, it is possible to trace the attackers.
Step 3: Count the amount of your stolen funds and keep related evidence
Protect the scene. Keep related evidence: cut off the network without shutting down your device, keep screenshots, audio recording and screen recording, and so on, for the follow-up trace to preserve clues. Then wait for professional forensics staffs for forensic analysis and count the amount of your losses.
Step 4: report the case to the law enforcement agency
Prepare relevant documents and materials and go to the law enforcement agencies to report your case.
Step 5: continue to follow up and maintain communication
Ask the law enforcement agencies about the progress of the case. Contact security companies for assistance if needed.
5 What are the guidelines for ordinary users for prevention of crypto theft?
Private key & Seed Phrase
The private key compromise is the most important type of problem. If it is compromised, it means that you lose all ownership of your wallet and that the other party has complete control over the transfer of any assets in your wallet.
Ways to steal private keys:
Private keys connected to network
Many users store their private key in plaintext directly on their cloud drive. If your cloud drive password is leaked, or even if a third-party online company leaks data, it could lead to the exposure of your private key. Even if you store it locally on your device, such as in a computer notepad, or in a mobile phone album via screenshots, there is a risk that your private keys will be leaked if your device is lost, or if hit by a Trojan horse virus. Account leaks can also lead to the exposure of seed phrases, so plaintext storage in devices with network are at risk of leakage. In addition to this, many users copy and paste their private keys when logging in, which also poses a risk of leakage in the process.
Fake websites steal private keys
Many users will search for keywords on Google to access trading platforms such as Opensea, but there will be a lot of fake sites to entice you to click on, even the fake sites rank higher in search results than the real ones. These sites look as good as the real ones. The UI styles and functions are similar to the real ones, and the domain names are very similar, when you open these sites, you will be asked to log in with your "wallet". They will often be paired with a fake wallet on the site. When you log in with a mnemonic, your assets will be moved in a flash.
Lost of private keys
In addition to the theft of assets by hackers, the loss of assets by users who lose their private key should not be underestimated. Many users record their private key in a computer notepad or write it down on a note, which may eventually lead to the loss of the private key when the computer is scrapped or lost, thus making it impossible to retrieve the assets. It is likely that a large number of bot addresses that currently hold assets but have not been traded for a long time are the result of lost private keys, and that these assets will be completely locked up.
Solutions to avoid private key issues:
Store private keys correctly and safely
Seed phrases or private keys should not be saved over a network. Do not store it directly in plain text on a cloud drive, do not transmit them through channels such as email, and do not save it in plaintext locally. It is best to save them offline. You can also use multi-signature wallets and smart wallets to save them. As the concept of account abstraction comes to fruition, more and more smart wallets are equipped with capabilities such as social recovery, which is also a big step forward for the safe storage of assets.
Copying and pasting seed phrases in sections
Avoid copying and pasting complete seed phrases by copying in sections. If necessary, you can copy in sections. After copying one section, copy something else, then continue to copy another section.
Careful when entering private keys or mnemonics
In all cases where you are asked to enter a private key, you can first assume that it is a phishing site and use it in conjunction with security extensions such as Beosin Alert and MetaShield, which will include a blacklist library to assist you in your judgement. The image below shows a fake Coinmarketcap website identified by Beosin Alert.
Download Beosin Alert, an anti-phishing browser extension: https://chrome.google.com/webstore/detail/beosin-alert/lgbhcpagiobjacpmcgckfgodjeogceji?hl=en
Phishing Websites
Common tricks of phishing websites:
Airdrops
If you check your NFT in Opensea, you should fifind a lot of NFTs you have never seen before in the hide section, and even offers with very high prices, there may be hackers airdropping NFTs to you to lure you into phishing sites. The scheme is actually to lure you to open the airdrop NFT site, and then steal your assets via signature approval, airdrop is only a means to lure you to open the site.
Discord DM
It is common in Discord to receive some DMs impersonating the official, telling you to get a certain NFT free mint rights, and then the following will come with a phishing URL. If you click on the button 'mint', pay gas, approve assets, and then you will find your NFT was transferred away.
Fake Twitter account
Many upcoming NFTs may face the problem of being registered with fake Twitter accounts, and even these fake accounts have more followers than the real ones. For example, if an NFT project is not yet on sale, but its fake account suddenly announces the sale and puts up a phishing website, then a large number of users who have been looking forward to the project for a long time will be trapped.
Official Discord/Twitter compromised
This is the most dangerous method of distribution, such as the hacking of the official BAYC Discord server, and other projects where the official Twitter account has been compromised, sending official notices directly to lure people to click on the phishing website.
Search engine results
Phishing websites sometimes rank higher than real websites in Google for keywords as the domain names are similar.
Ways to Avoid Phishing:
Check the authenticity of sources
Look carefully at the source channel to see if it is official, check that the domain name is correct and think twice before you interact.
Be careful with all approvals, transfers and blind signatures
When your wallet asks you to approve and transfer assets, be extremely careful to check whether you really intend to perform such an operation at the moment, and that all blind signatures are done carefully. Check the content and source of the signature to ensure that the operation you are currently being asked to perform is indeed your intention.
Segregation of assets
Always have at least 2 wallets, 1 for small amounts of money for daily transactions, and another for larger amounts of money that you don't use very often, which should only be used to deposit money and avoid transactions as much as possible so that even if you experience a phishing incident, you will have limited assets stolen.
Install anti-phishing extension
Install security extensions such as Beosin Alert, MetaShield, etc.













Nice work
Good article