Wallet Drainers Starts Using Create2 Bypass Wallet Security Alert
Author: Scam Sniffer
Overview
Recently, we discovered that some Wallet Drainers are using Create2 to bypass security alerts in certain wallets. By exploiting Create2’s ability to pre-calculate contract addresses, the Drainers can generate new addresses for each malicious signature. These addresses are deployed after the victim signs the malicious signature.
After noticing these abnormal transactions, we suspected that this method was used to bypass wallet security alerts. Subsequent tests confirmed our suspicions. The drainer associated with this has stolen nearly $60 million from around 99,000 victims in the past six months.
After a discussion with SlowMist team, a group has employed the same technique in Address Poisoning to steal $3 million from 11 victims since Aug. One victim lost up to $1.6 million.
Suspicious Transaction
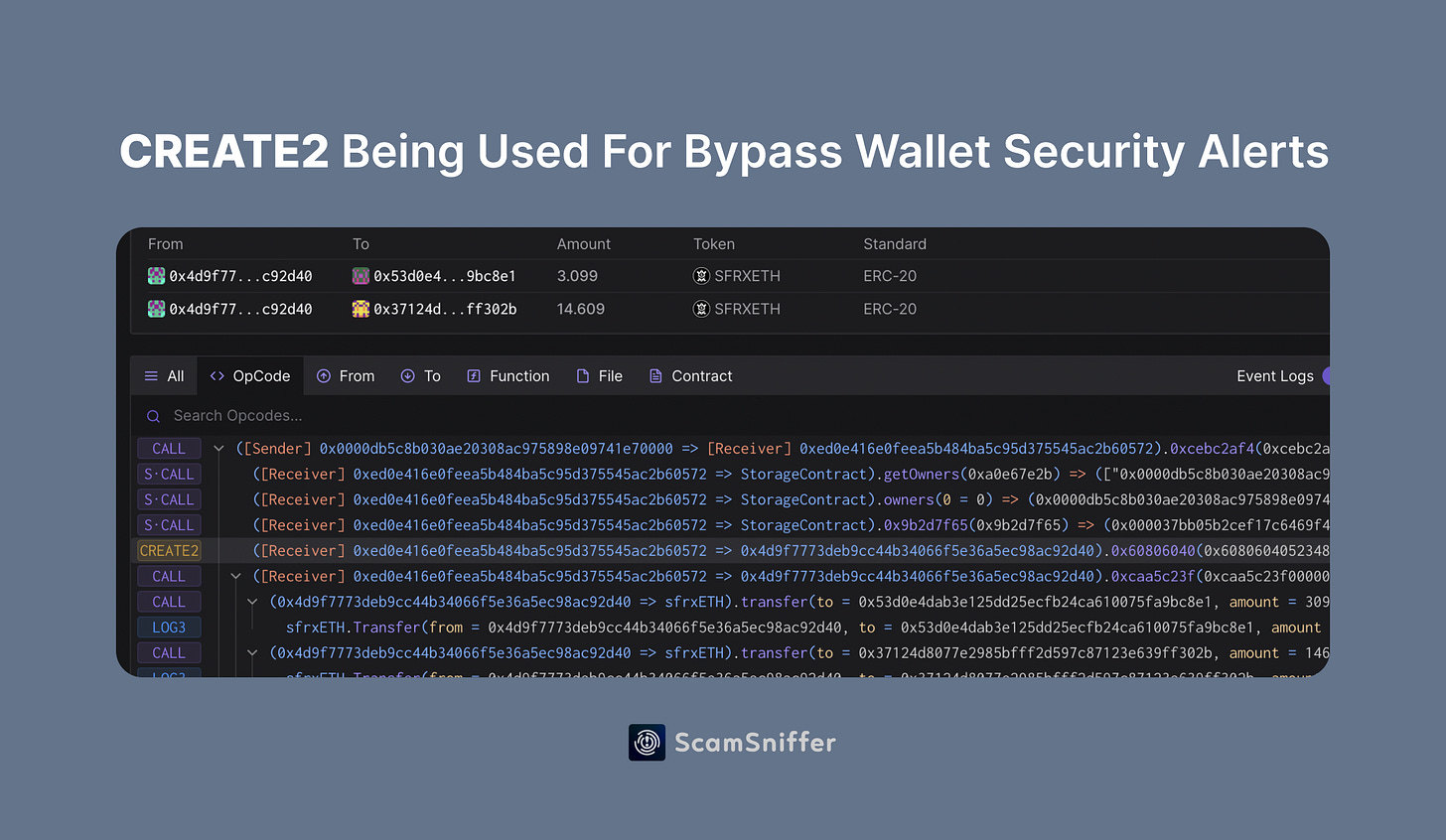
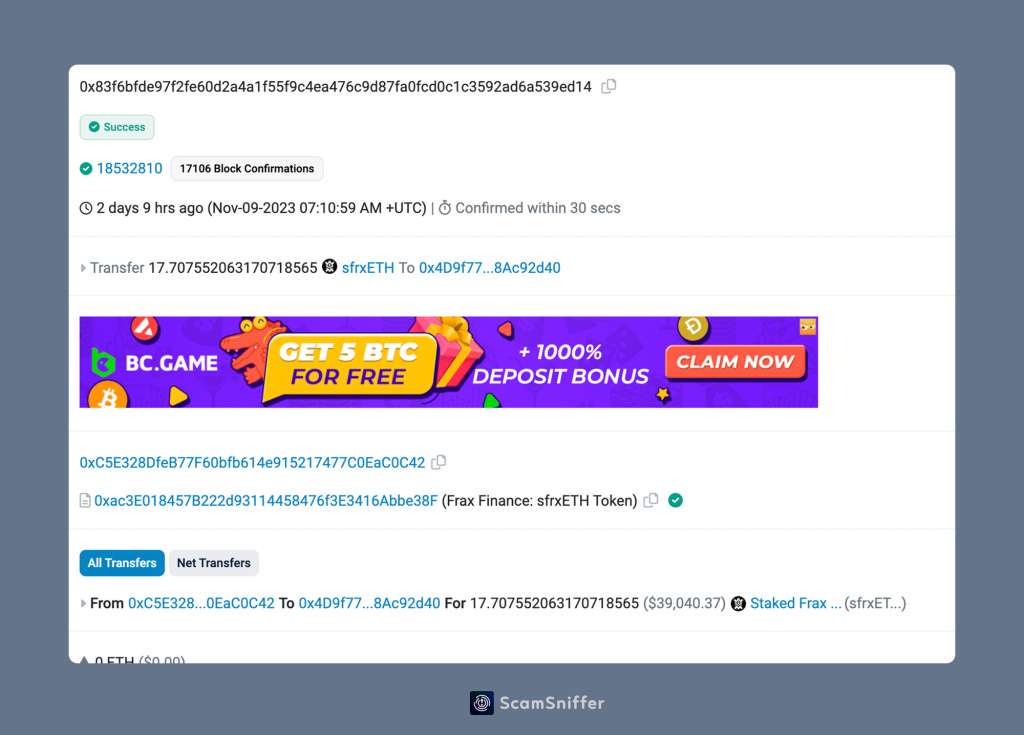
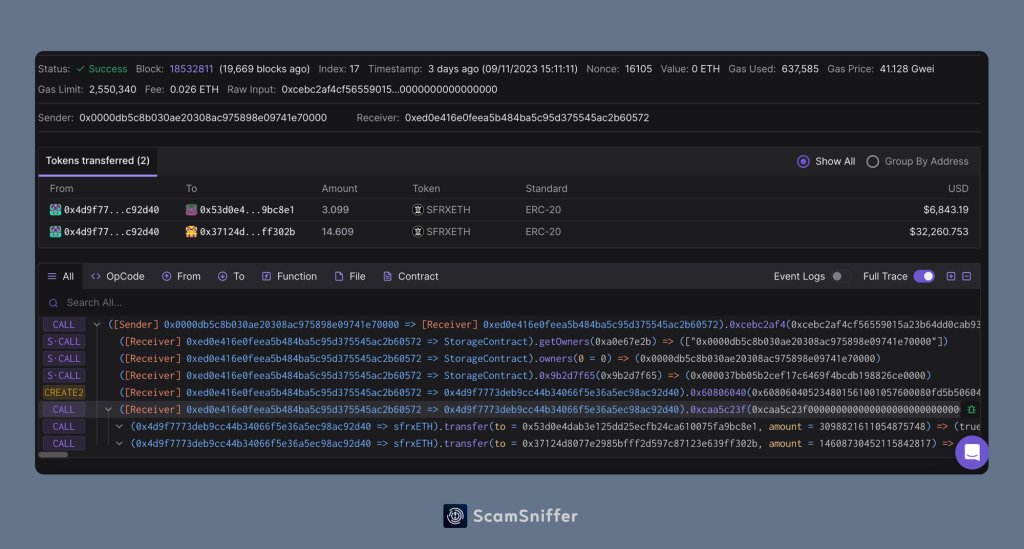
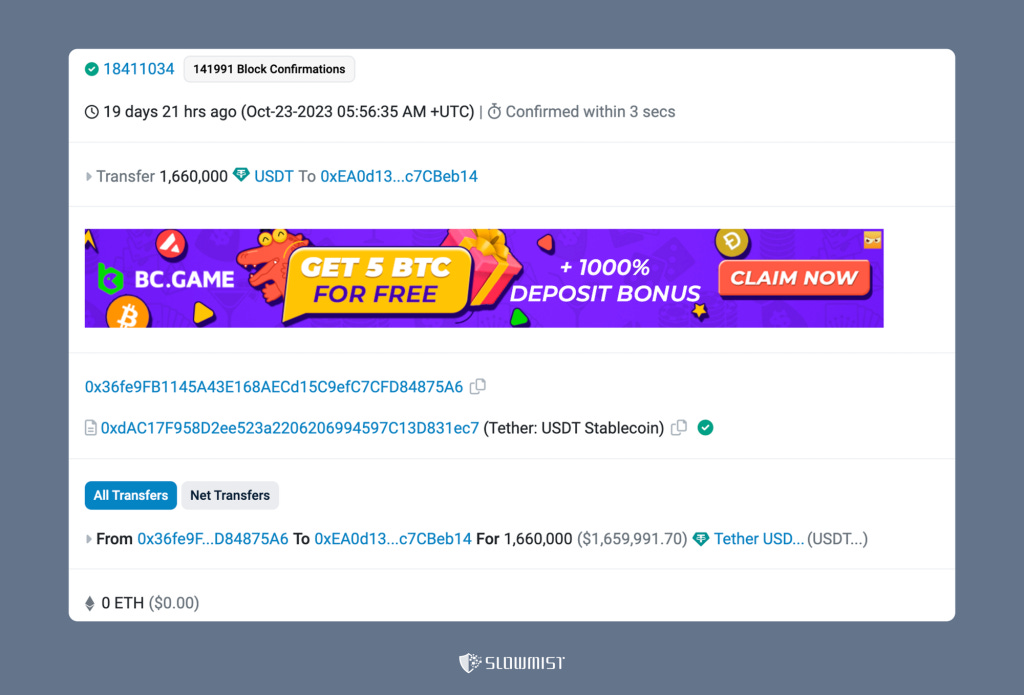
In this transaction, the victim directly transferred their sfrxETH to 0x4d9f7773deb9cc44b34066f5e36a5ec98ac92d40.
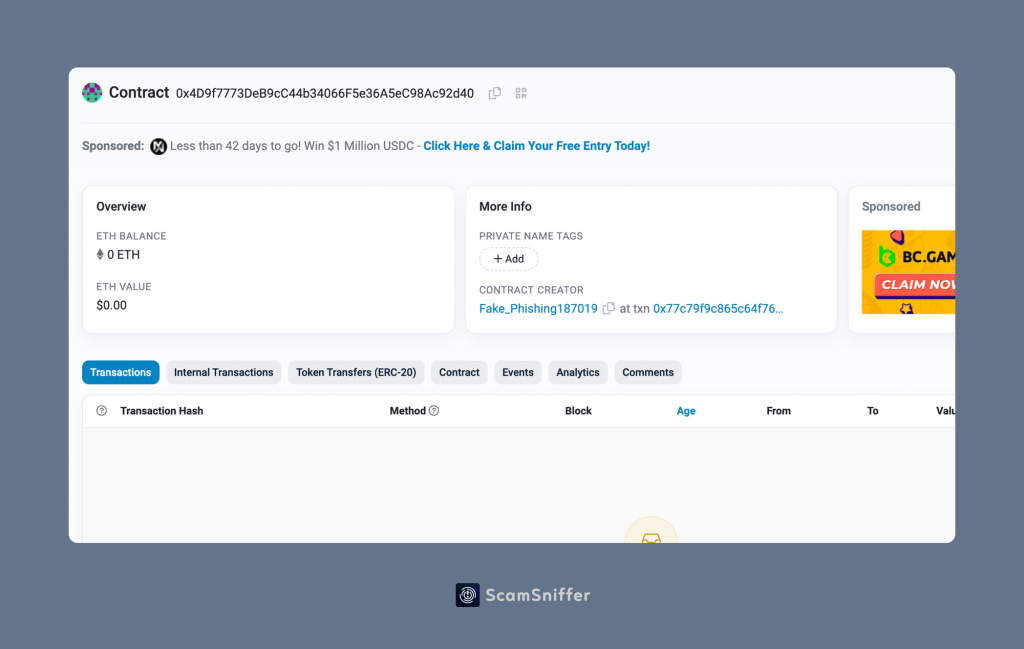
But if we open this address, there are no previous transactions associated with it, and this address is a contract.
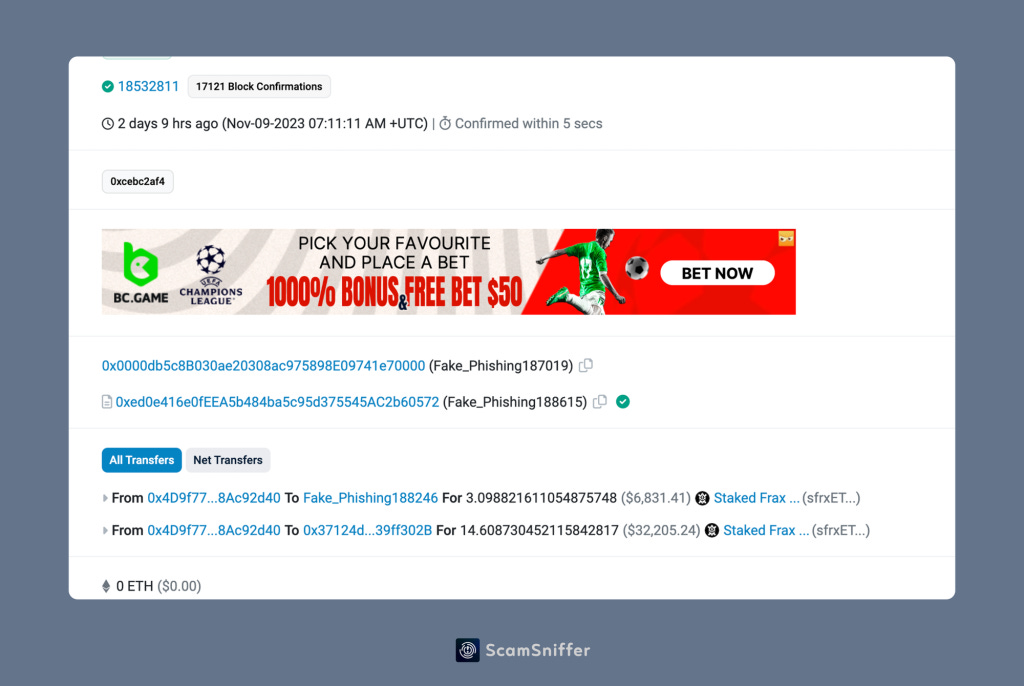
By opening the contract creation transaction of this address, we can see that this transaction is also used by the Drainer to transfer the stolen assets.
Looking at the call trace of this transaction, it can be seen that 0x4d9f7773deb9cc44b34066f5e36a5ec98ac92d40 was created after the call to create2.
What is Create2
The CREATE2 opcode allows us to predict the address of a contract before it is deployed on the Ethereum network. Uniswap uses CREATE2 to create Pair contracts.
Unlike the CREATE opcode, the calculation of the contract address with CREATE2 no longer relies on the account’s nonce, but instead calculates a new address based on the following parameters:
Creator’s address (
address)Confusion value as a parameter (
salt)Contract creation code (
init_code)
The specific calculation formula is as follows:
keccak256(0xff ++ address ++ salt ++ keccak256(init_code))[12:]Read more: WTF Solidity: 25. Create2
This means that based on CREATE2, the Drainer can easily generate temporary new addresses for each malicious signature. After the victim signs the signature, the Drainer creates a contract at that address and transfers the user’s assets.
As for the motivation behind this, we suspect it is to bypass some wallet security checks. A new address means that there is no meaningful information on the chain to judge the risk of the address.
Bypassing Security Alerts
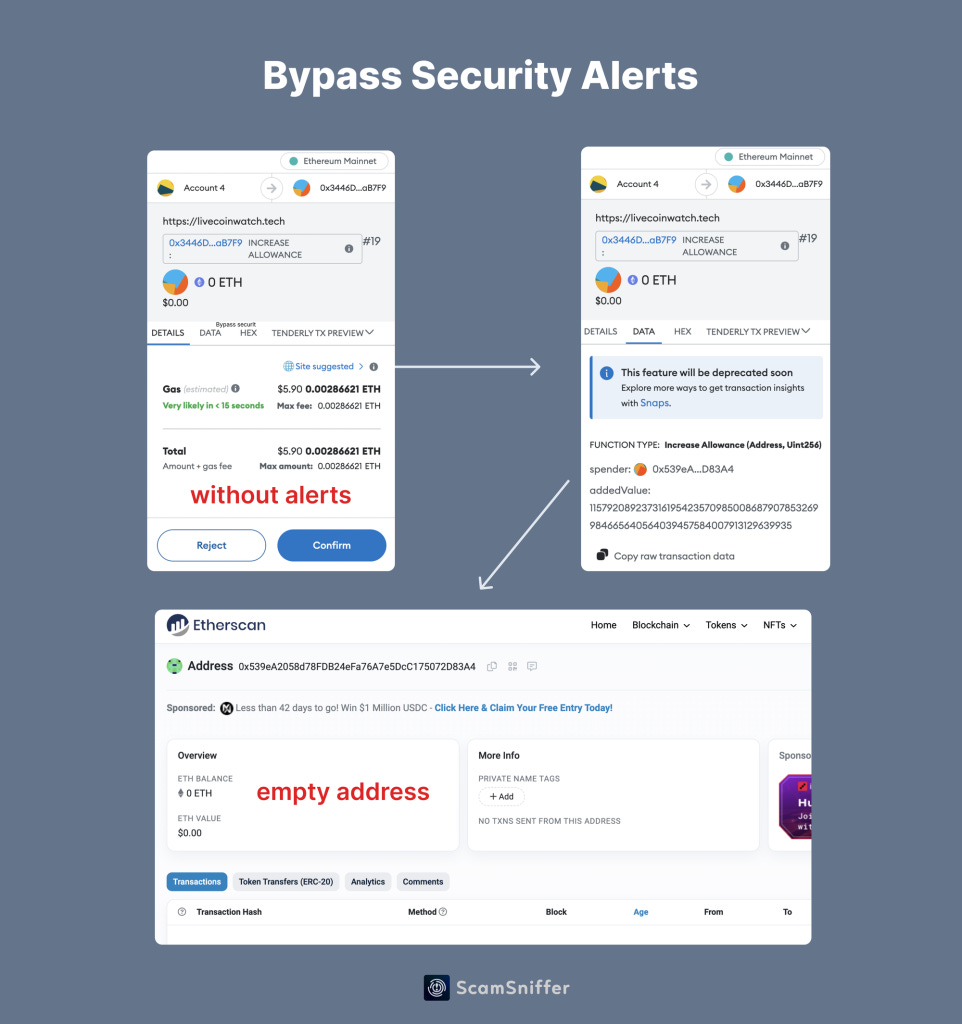
Then we tested some phishing websites associated with Drainers in Scam Sniffer’s database and found that they successfully bypassed the wallet’s security alert using this method.
As shown in the image:
The phishing site initiated a malicious signature for Increase Allowance.
The spender is the address pre-calculated by the Drainer.
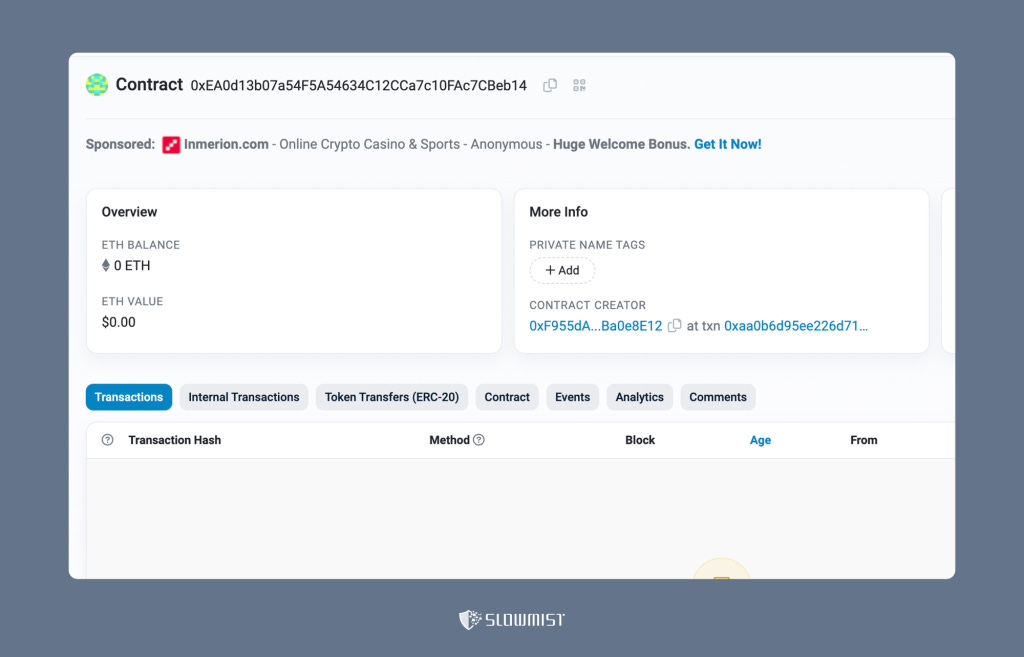
So, when we open the spender, we can see that it is an empty address.
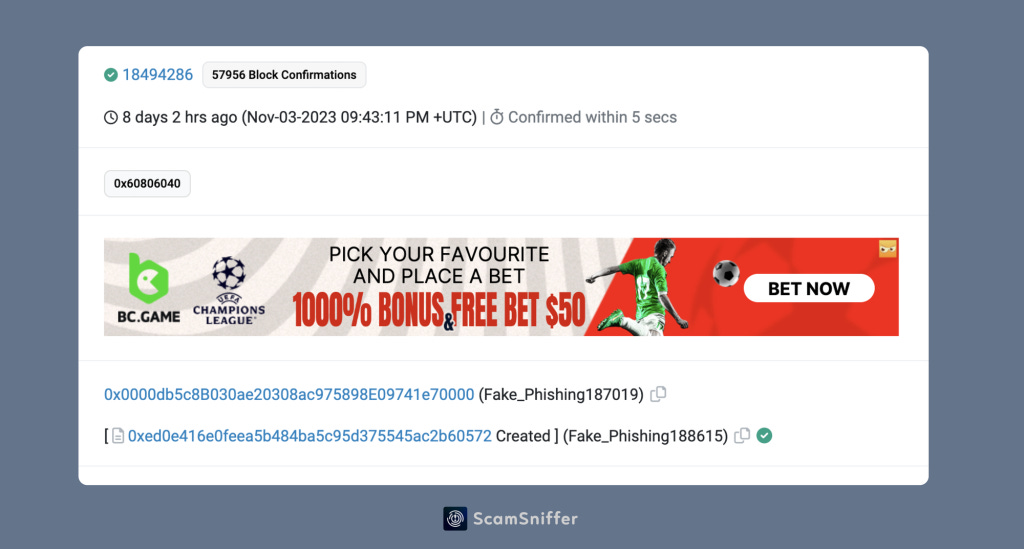
In the suspicious transaction, the related contract 0xed0e416e0feea5b484ba5c95d375545ac2b60572 with create2 was deployed 8 days ago
Real Case
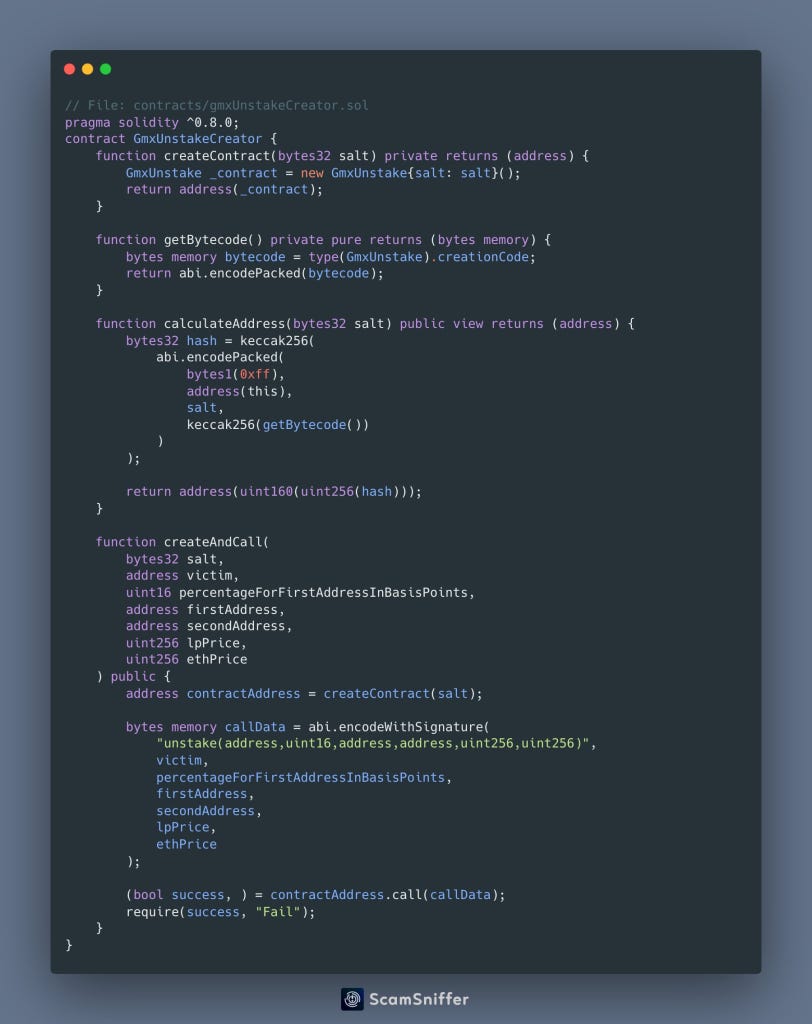
Check this smart contract used in real case
call
calculateAddresspre-compute the address.call
createAndCallcreate the contract and transfer the tokens
Address Poisoning
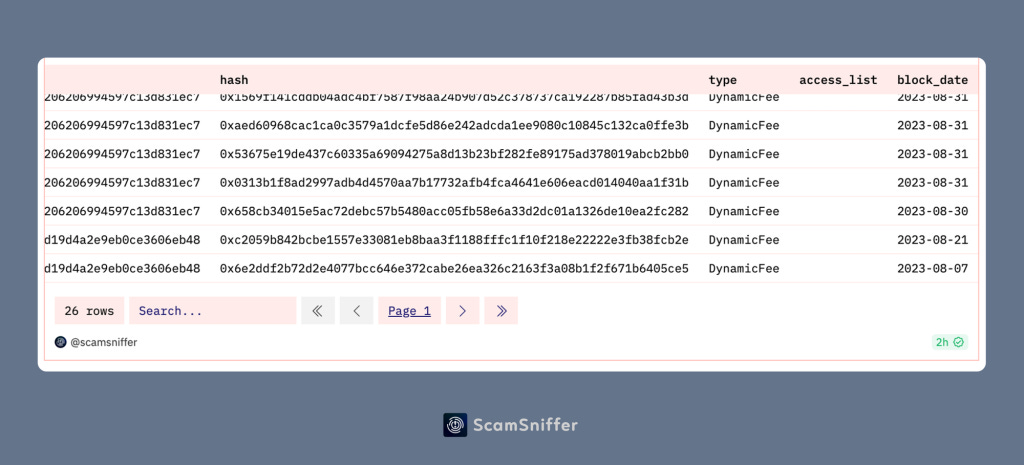
After discussing this discovery with the SlowMist team, they shared a similar application of this technique in address poisoning phishing: a group has been using Create2 since August to continuously steal nearly $3 million in assets from 11 victims, with one victim losing up to $1.6 million.
Attackers can use the address calculation method of create2 to offline pre-generate a large number of addresses and then extract addresses similar to the targeted ones to initiate fake transfers for address poisoning phishing.
keccak256(0xff ++ address ++ salt ++ keccak256(init_code))[12:]A victim mistakenly transferred $1.6 million to an address similar to the one they had recently transferred to.
This contract was also created in the transaction for transferring assets.
Through on-chain data analysis, we can see that this same method can be traced back to August.
And there is an address poisoning phishing case near this date, Binance sent $20m to an address but has frozen them luckily.
Conclusion
Based on the above cases, we can see that Create2 is now being used in various phishing attacks. Based on the ability to pre-calculate addresses with Create2, it can be used to create temporary addresses to bypass wallet security detection and generate a large number of addresses for address-poisoning phishing attacks.
Finally, Hope you are staying safe! the cat-and-mouse game of detection and counter-detection will never stop. always don’t trust it, verify it!